Log in to myMicrochip to access tools and benefits. Sign up in just one minute.
Maximize Your Experience: Reap the Personalized Advantages by Completing Your Profile to Its Fullest! Update Here
Stay in the loop with the latest from Microchip! Update your profile while you are at it. Update Here
Complete your profile to access more resources.Update Here!
Why Would You Harden Your IoT Security with the ATECC608A for Google Cloud IoT Core?
Google Webinar on Security with the ATECC608a and Cloud IoT Core
Check out how to improve IoT security by securing the authentication between Google Cloud IoT core and IoT devices using a secure element (ATECC608A) from Microchip.

Cloud IoT Core Authentication Use Case
Hardware-Based Root of Trust for Google Cloud IoT Core
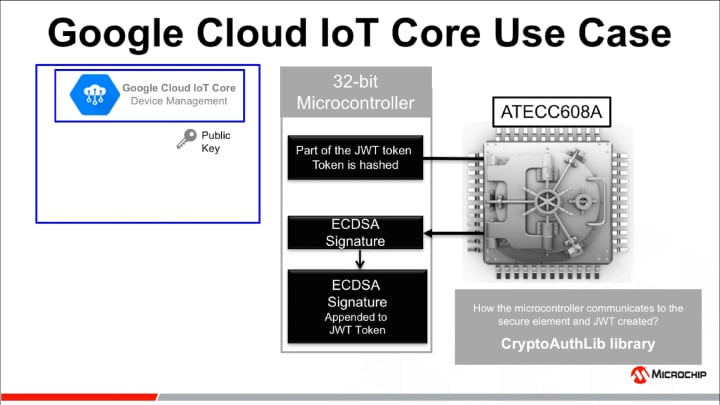
In this use case, we illustrate how the ATECC608A combined with Google Cloud IoT Core from Google Cloud Platform enables secure authentication. The philosophy with secure elements in IoT is to provide a unique, trusted and protected identity. To achieve the objective, the identity provisioned to the hardware must be genuine and the cloud platform needs to be able to trust it. Consequently, a chain of trust must be created.

Google IoT Core ATECC608A
20 Years of Experience in Secure Provisioning

Prototype
- Educate yourself about the Google Cloud IoT Core Security model for light embedded systems
- Understand why private key isolation is vital to your design
- Learn how CryptoAuthLib manipulates the JWT token
- Learn how to configure the memory zone and set your expected policies
- Learn the basics of provisioning a secure element

Personalize
- Memory configuration is defined and locked
- Your Certificate Authority is decided
- Google Cloud IoT Core production account is configured with Google Cloud Platform
- Secret exchange with Microchip completed
- The ATECC608A is set up with your customized part number

Mass Production
- All the provisioning—keys/certificates generation and manipulation—is done within Microchip's secure factories
- Keys are internally generated and never exposed to the outside world; it’s zero touch
- Elimination of any software or manufacturing backdoors
- The device ships pre-provisioned with the secrets




