Qi® 1.3 and Qi 2.0 Wireless Charging Specification - Part 2
This is a two-part blog where we discussed in part one the foundational reasons why secure authentication is added to the WPC 1.3 and 2.0 specification. In this, part two, we will discuss how to ensure secure authentication.
Establishing Trust Between the Phone and the Charger
Let’s now break out in two parts what needs to happen to implement trust between the phone and the charger. First, we review how the trust is established between the phone and the charger. Then, we look at what needs to happen during manufacturing to create and protect that trust.
When the phone authorizes the charger to do its job, the phone will first request an X.509 certificate from the charger and verify that it is part of a certificate chain built from a root certificate authority (root CA) chosen by the WPC. Additionally, the charger must have an associated private key that is used to sign a challenge issued by the phone proving knowledge of a secret without ever compromising the secret. The private key is bound to the customer specific certificate chain governed by the WPC. The Qi 1.3 and Qi 2.0 standard mandates the private key to be stored and protected by a certified Secure Storage Subsystem (SSS). Both the ECDSA sign algorithm and the private key must be within the same physical secure boundary to ensure a trusted authentication (Figure below).
4. WPC Requirements for Secure Storage Subsystems (a.k.a. Secure Elements) A Secure Element Device protects the private key that is associated with a signed Product Unit Certificate. Extraction of the private key will make it possible to use the signed Product Unit Certificate in products that are not Qi Certified and that creates a safety risk for the users of that product. Annex A, Sec 3.1 Secure Elements must be certified with one of the following methods: · Provisioned Secure Storage Subsystems shall have a JIL Rating of High (“TOE resistant to attackers with attack potential of High”) as defined in “Application of Attack Potential to Smart Cards” version 3.1 or later which requires review of the design, test and attack resistance of the SSS TOE. A lab accredited by a SOGIS member in the domain of smart cards and similar devices must perform the white box vulnerability assessment according to the afore mentioned JIL standard. A summary report written by the accredited lab must be available to the WPC and Qi charger manufactures to indicate that a JIL Rating of High has been achieved. ·Secure Element Devices shall be built on a hardware which is certified according to CC EAL4+ Protection Profile PP0084 or PP0035*, or comparable profile. |
WPC Qi 1.3 Specification Abstract
If the private key is anywhere other than in the SSS, there is no trust in the key. As the specification mentions, the SSS must prove its robustness to protect cryptographic keys. This is what the Joint Interpretation Library (JIL) scoring system and rating which is widely recognized in the Common Criteria community is all about. It focuses on evaluating the secure key storage strength of a semiconductor device, generally called secure element. The JIL vulnerability assessment is used to determine an AVA_VAN.x rating as part of a larger EAL rating. To achieve a certain AVA_VAN.x and EAL level, the device must meet a corresponding JIL level. Microchip secure elements (or SSS in WPC terms) recommended for Qi 1.3 and Qi 2.0 chargers meet the highest JIL rating with a JIL level “High”. Below are some of the criteria that go into determining a JIL rating:
- How much time is required to break the algorithm?
- What level of skills must an attacker possess?
- What knowledge of the Target of Evaluation (TOE) is needed to achieve a successful attack?
- How difficult is it to get samples of the TOE and how many are needed?
- What type of equipment is needed for a successful attack?
In technical terms, the charger which contains the SSS will perform an ECDSA P256 sign operation of the challenge sent by the phone which will output a signature. This a simple one-way authentication from the phone to the charger. The charger doesn’t authenticate the phone.
Before the charger is sold to the market, there are couple of steps to create and protect trust during manufacturing. The goal is to remove any exposure to the private keys involved in building the chain of trust. First, to create a chain of trust, all the private keys involved must be in a hardware secure module (HSM) or SSS at the charger level. If the private keys must always exist in a piece of hardware such as the HSM or SSS, how are they generated, stored and chained together? That’s achieved through the WPC “key ceremony”.

The following infrastructure must exist for the key ceremony to take place:
- The third-party root CA company selected by the WPC creates a root certificate and it’s associated root private key that signs the manufacturer Certificate Signing Request (CSR). The manufacturer certificate will be unique to each wireless charger company and the product certificate is unique to every charger.
- The manufacturer CA (MFG Cert) is the company approved by the WPC who will create the manufacturer certificate and protect its associated private key in a certified HSM inside its factory.
- The wireless charger has the product certificate. The associated public/private key pair is generated and protected by the SSS during manufacturing of the SSS. The private key is provisioned inside the SSS within a secure supply chain. The SSS sends a CSR to the manufacturing CA that is already signed by the root certificate.
The WPC calls the process a key ceremony and this happens once a month every third Thursday of the month (as of 2021). The chain of trust is now cryptographically established without exposure to external contract manufacturers or third parties. Now, there is trust created between WPC, the phone and the charger. The WPC can trust the phone which can trust the charger.
How does Microchip help with Qi 1.3 and Qi 2.0 compliance?
The WPC has defined a detailed engagement process to follow illustrated below.
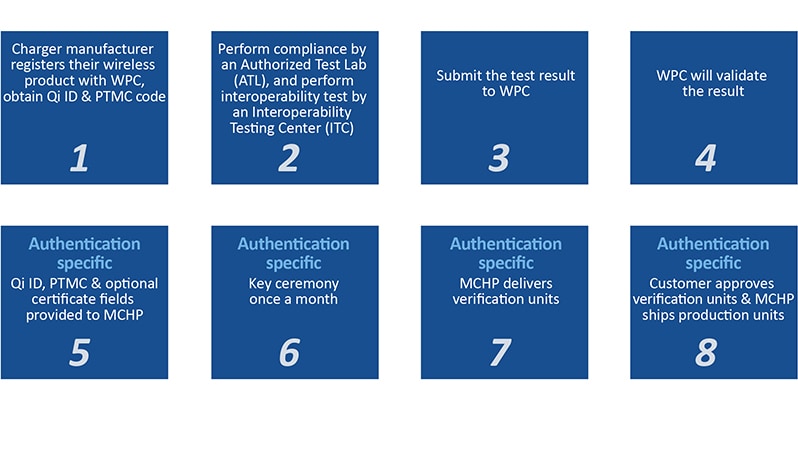 To start, the transmitter manufacturer must be a member of the WPC and sign an additional manufacturing license. The part of the process that’s specific to the secure storage subsystem enrollment consists of providing your company name, PTMC code, Qi ID, and manufacturer sequence IC to Microchip which are assigned by the WPC. If the information is accurate and provided in due time prior to the key ceremony scheduled by the WPC, Microchip will then handle the key ceremony operations with no technical involvement from the customer. We will provision the SSS inside our HSM equipped factories and ship your securely provisioned SSS to the specified address(es). Nowhere in this process, has the charger private key been exposed outside the physical secure boundary of the SSS.
To start, the transmitter manufacturer must be a member of the WPC and sign an additional manufacturing license. The part of the process that’s specific to the secure storage subsystem enrollment consists of providing your company name, PTMC code, Qi ID, and manufacturer sequence IC to Microchip which are assigned by the WPC. If the information is accurate and provided in due time prior to the key ceremony scheduled by the WPC, Microchip will then handle the key ceremony operations with no technical involvement from the customer. We will provision the SSS inside our HSM equipped factories and ship your securely provisioned SSS to the specified address(es). Nowhere in this process, has the charger private key been exposed outside the physical secure boundary of the SSS.
How does Microchip help with Qi 1.3 and Qi 2.0 compliance?
.jpg)
Note: The WPC only requires a single certificate chain and JIL High - All other use cases are customer preference.
*ECC608 maximum operating temperature is 85C
Microchip provides various SSS solutions to comply with the Qi 1.3 and Qi 2.0 mandated authentication requirements depending on the market segment and system cryptography needs. Four solutions are offered today:
- For consumer applications, the TrustFLEX for WPC ECC608 (ECC608-TFLXWPC) and the cost optimized ECC204
- For automotive applications, the Trust Anchor TA100 and cost optimized TA010
Paired with our secure silicon devices, we provide a library called CryptroAuthLib available on Github which lives within the microcontroller. The library will handle the callbacks (challenges) the microcontroller will send to the SSS which will provide a response (signature in the WPC use case).
 The SSS can be swapped in a reference design without impacting the certification, but the dependency is on the library that will be integrated in the MCU code. It is important to make sure the solution you choose offers a properly supported and maintained library integrated within the application code. The SSS alone doesn’t certify a Qi 1.3 and Qi 2.0 solution, it only helps to meet the new mandated authentication.
The SSS can be swapped in a reference design without impacting the certification, but the dependency is on the library that will be integrated in the MCU code. It is important to make sure the solution you choose offers a properly supported and maintained library integrated within the application code. The SSS alone doesn’t certify a Qi 1.3 and Qi 2.0 solution, it only helps to meet the new mandated authentication.
How does Microchip help you meet full certification?

Welcome to the one-stop-shop Qi 1.3 and Qi 2.0 reference design provider. Microchip takes care of all the above and offers competitive turnkey reference designs for both automotive and consumer grade designs. Our 15W reference designs have passed the WPC certification and include the maintained support of CryptoAuthLib. They integrate a dsPIC33 Digital Signal Controller (DSC) and a complete bill of materials including the necessary analog devices. The flexible software architecture of the solution provides enhanced Foreign Object Detection (FOD) and proprietary fast charging capability. In addition, as an approved manufacturer CA by the WPC, Microchip handles the entire key ceremony for our customers removing this hurdle from your hands.
The new upcoming wireless chargers are on the right path to deliver a safer and more reliable user experience than ever before. The trust label the WPC brings to this market will ensure the high-quality expectations continues to be met by this technology.
In part one, we discussed why the secure authentication was added to the Qi WPC1.3 and Qi 2.0 wireless charging specification. Finally, make sure to check out the step-by-step process for triggering the key ceremony.
Resources
Qi 1.3 Reference design :https://www.microchip.com/en-us/solutions/technologies/power-conversion/wireless-power
Consumer Secure Storage Subsystem: https://www.microchip.com/en-us/product/ecc608-tflxwpc
https://www.microchip.com/en-us/product/ecc204
Automotive Secure Storage Subsystem: https://www.microchip.com/en-us/product/ta010
Microcontroller: https://www.microchip.com/en-us/product/dspic33ck256mp506
Trust Platform Design Suite: Download
