Understanding the ISA/IEC 62443 Standard and Secure Elements
Microchip’s secure elements and accompanying Security Pattern services are designed to provide the guidance required to comply with ISA/IEC 62443 and achieve device certification.
Deciphering the 800-plus-page ISA/IEC 62443 series of standards for Industrial Automation and Control Systems (IACS) is not for the faint of heart. Although industrial companies have been looking at a fragmented set of various security standards for their products, the ISA/IEC 62443 is the first comprehensive set of guidelines that focuses on risk assessment and addresses security at all stages of design and development. With cyberattacks on IACS increasing exponentially every year, meeting the requirements defined by the ISA/IEC 62443 can assure asset owners, system integrators, and product suppliers that they have assessed risks and have preventively identified and applied countermeasures to reduce vulnerabilities to tolerable levels.
When it comes down to semiconductor devices, one of the critical requirements within ISA/IEC 62443 is its attention to cybersecurity at the component level, focusing on performing comprehensive risk assessments throughout the design, development, and procurement processes. As we’ll see, Microchip’s secure element devices such as the ATECC608 and TA100 are key enablers of security at the component level and help ensure compliance and certification of IACS products. To understand why, we need to delve into ISA/IEC 62443 and how it addresses cybersecurity.
Getting to Know ISA/IEC 62443
To make informed decisions about the design and operation of an IACS, it is necessary to conduct thorough risk assessments that address threats, vulnerability, and potential consequences. Until recently, there have been few resources available for guidance about how to conduct such an assessment. Although companies like Security Pattern provide this as a service, it is important for asset owners, system integrators, and product suppliers to understand how to perform these steps themselves and apply the results to determine where to best apply resources and focus their design decisions. The IEC 62443-3-2 series of standards provides this guidance and gives IT and OT common ground to work together, with OT focusing on the assets required to communicate and IT focusing on cybersecurity expertise and technology.
ISA/IEC 62443 consists of 14 work products grouped in four tiers (general, policies and procedures, the system, and components), as shown in (Figure 1. Fortunately, if your company makes or supplies products, the most relevant part of ISA/IEC 62443 is the one that covers components -- Tier 4 -- that focuses on security-related requirements for products and processes and their management.

ISA/IEC 62443 is built on the security levels shown in Figure 2 that define the protection level provided against attacks. This ultimately results in a risk assessment that reveals a Target Security Level (SL-T) for the standard as a whole. Based on this SL-T, the asset owner and system integrator can then buy subsystems and components and implement the IACS to meet the security needs of the system. Each component and subsystem is characterized by a Capability Security Level (SL-C). The system implementation is evaluated by the asset owner to verify whether the product’s required security level is being met. 
Exploring the Component level: IEC/ISA62443-4
ISA/IEC 62443 requires product suppliers to apply security-by-design principles including defense-in-depth as well as proper definition and tracking of security requirements from conception through design, implementation, testing, managing of field issues, and decommissioning. Tier 4 (IEC/ISA 62443-4) includes two subsections, 62443-4-1 (Secure Product Development Lifecycle Requirements) and 62443-4-2 (Technical Security Requirements for IACS components).
As part of the certification journey to ISA/IEC 62443, the product manufacturer must meet the requirements of 62443-4-1 and adopt processes that guarantee its products are managed with a level of security commensurate with their technological content, in keeping with customer expectations, and are sustainable throughout the product’s lifecycle. The product must also satisfy the requirements of 62443-4-2 (Part 4-2) that defines component requirements and ranks their security to one of four Capability Security Levels (SLCs).
The product’s SLC must be evaluated, and a security level applied to it. This evaluation is based on a list of Component Requirements (CRs) and their associated Requirement Enhancements (REs). They are grouped in categories called Foundational Requirements (FRs) as shown in Table 1. This evaluation must be repeated across all CR/RE groups belonging to each FR category and the total security level for the product is the minimum security level it achieves through all the evaluations. 
An FR is a group of sets, each consisting of one CR and likely some REs. This gets a bit dense, so I will use an example to illustrate how this works. Table 2 shows an evaluation based on component requirement CR1.7 that covers “strength of password-based authentication” and is contained in the first FR category (Identification and Authentication Control). There are two REs associated with CR7.1. 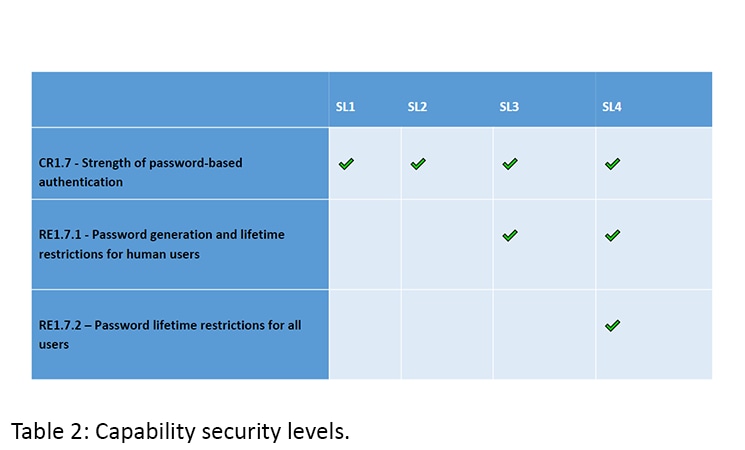
If the component satisfies all component requirements of CR1.7 its security level will be 1. If it satisfies CR7.1 and the first RE (RE1.7.1), its security level will be 2. If it satisfies CR1.7 as well as what is required in RE1.17.1 and RE1.7.2 its security level will be 4, making it the most secure. This evaluation must be repeated across all CR/RE groups belonging to each FR category. The total security level for the product is the minimum achieved throughout all evaluations.
The Benefits of Secure Elements in IEC/ISA 62443
The ISA/IEC 62443 standard often refer to secure key storage or protection of the cryptographic keys. Cryptographic algorithms are instructions employed to perform a mathematical function, and without the protection of their associated keys which are triggering the math, there is virtually no security at all, so secure key storage becomes immediately essential. This is where secure elements like the ATECC608 and T100 begin to contribute to successful certification.
Secure key storage protects both cryptographic operations and cryptographic keys within a physical boundary within a device. The keys and algorithms must be contained in the same secure boundary in the device so they cannot be exposed during transactions. The robustness of the secure key storage is tested in conformance with the Common Criteria Joint Interpretation Library (JIL) rating scale that defines robustness of key protection.
Microchip’s Trust Platform provides a simple way for asset owners to implement secure authentication of hardware devices and provides a secure system to manufacture device keys. The pre-configured TrustFLEX ATECC608 secure element can be paired with any microcontroller and microprocessor and for rapid prototyping of secure solutions, you can use the Trust Platform Design Suite that includes a guided “use case tool,” and other resources.
Streamlining Security During Manufacturing
Handling the cryptographic keys following a secure manufacturing process is also essential to preserve as much isolation between keys and outside variables. For example, Microchip’s manufacturing facilities are equipped with a network of managed hardware secure modules (HSM) that let customers use our secure key provisioning service infrastructure that’s already amortized
When you enable a secure element such as the ATECC608 or AT100 with this service, you follow a secret key exchange process that binds the credentials securely stored in the device to their chain of trust without exposing the cryptographic keys to any third party, such as a contract manufacturer. If you want to activate the cryptographic keys during late-state provisioning, the secure element can accommodate that as well.
Microchip’s services make the otherwise difficult process of key provisioning secure, simple and cost efficient. Support is provided to component manufacturers for understanding their products’ security requirements and how they relate to ISA/IEC 62443. We also help define and refine security-related requirements including platform definition and selection and guide you in making proper usage of Microchip components and their set of security features.
During product development, Microchip has chosen to partner with Security Pattern to help define your system and streamline production flow including supply chain security with third-party suppliers and software development. We can also provide guidance to set up your public key infrastructure, digital certificate management, secure boot and many other use cases. Other support services from Security Pattern include performing a product gap analysis and comparing it to ISA/IEC 62443-4-2 component requirements, help you work with an ISA/IEC 62443 certification body, and provide training sessions. Microchip and Security Pattern collaborated to create the AN3983: Demystifying ISA/IEC62443 and Secure Elements that take the IEC 62443-4-2 component level part of the standard and maps the Component Requirements (CR) to the relevant functions and features of Microchip secure elements.
Selection Matrix from AN3983 for Secure Element Feature vs. IEC62443 Specifications

In summary, the advantages of using a device with a secure element cannot be overstated because, without it, your system will hardly be truly secure. Microchip’s secure elements and accompanying Security Pattern services are designed to provide the guidance required to comply with ISA/IEC 62443 and achieve device certification. Make sure to consult the detailed application: “Demystifying IEC/ISA 62443 and secure elements” where we provide a thorough navigation guide of the standard and pinpoint exactly what features of the secure element help meet a specific line item in the standard.
Resources
[1] https://isasecure.org/certification/iec-62443-csa-certification#tab1
[2]https://isasecure.org/certification/iec-62443-csa-certification#tab2
[3] AN3983: Demystifying ISA/IEC62443 and Secure Elements
Make sure to visit our Trust Platform for CryptoAuthentication devices for more and information as well as Security Pattern site for consulting services.
Check out the SHIELDS UP! security webinar about IEC62443 and secure elements where Security Pattern goes over the architecture of the specification.
Authors:
Xavier Bignalet - Microchip Technology
Matteo Giaconia - Security Platform
