Security with The Things Industries Join Servers
To make adding hardware secure key storage easier, the secure element is paired with The Things Industries' (TTI) join server service for turnkey secure authentication. The corresponding AES128 authentication keys are also hosted and protected in TTI’s managed join servers. Through a claim procedure via the TTI portal, the protected keys in the secure element are “claimed” and then owned by the company. This process simplifies the cumbersome unsecure provisioning practice used without secure key storage. This join server is completely agnostic to the network server and/or application server providers to preserve business scalability by leaving freedom of choice to the architects. Flexibility doesn’t stop here, the ATECC608A-MAHTN secure element is a microcontroller-agnostic solution that adds true hardware secure key storage to any LoRa-connected products.
Benefits of Using The Things Industries Join Server for LoRa-Based Designs
- Add secure elements to LoRaWAN 1.0.x and 1.1
- One year of TTI join server access included
- Microcontroller-agnostic secure element
- Network and application server agnostic TTI join server
- Leverage Microchip’s secure provisioning service
- Ability to provide a unique, trusted, protected and managed identity
- Supported by Microchip and Arm® LoRaWAN stacks
- Pre-configured authentication, secure boot
- Re-keying capability between TTI join servers and the secure element
- JIL rated “high” secure key storage
- Protection against anti-tampering, side-channel attacks

How Does The Things Industries Join Server Service Work?
What Do You Really Get with this Configured and Provisioned ATECC608A for LoRa-Connected Applications?
What’s the Value of a Configured and Provisioned Secure Element for LoRa-Based Systems?
What’s the Importance of Secure Hardware Key Storage?
Start Developing your LoRa Solution with Two Hardware Options
Develop with the SAM R34 Ultra-Low Power LoRa SiP and Microchip LoRaWAN stack
- Step one: Purchase ATECC608A-MAHTN-T secure element samples and the socketed board AT88CKSCKTUDFN-XPRO
- Step two: Purchase the SAM R34 development board
- The user manual for the SAM R34 can help speed development
- Step three: Open a TTI account, activate the join server
- Step four: Claim the secure element(s) from the TTI portal
- Step five: Access the code and user manual
Develop with the SAM L21 MCU and Discrete Semtech Radio and Arm mBed™ OS LoRaWAN stack
- Step one: Purchase ATECC608A-MAHTN-T secure element samples and the socketed board AT88CKSCKTUDFN-XPRO
- Step two: Purchase the SAM L21 development board
- The user manual for the SAM L21 can help speed development
- Step three: Open a TTI account, activate the join server
- Step four: Claim the secure element(s) from the TTI portal
- Step five: Access the code and user manual
How to Build a Secure Provision Workflow - The Things Conference 2019
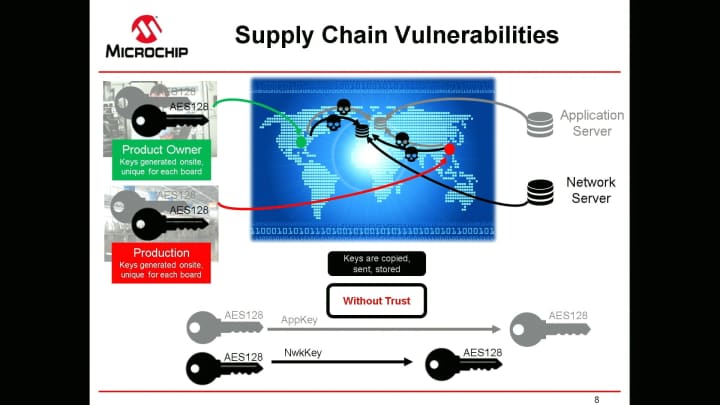
How to build a secure provision workflow and strengthen authentication to TTI’s join server. Manipulating application and network server keys is not only a daunting process but also opens backdoors in LoRaWAN connected products. Microchip’s secure element, bundled with TTI’s join server service, helps simplify the provisioning process and secures the keys, not only in the deployed system but also throughout the entire supply chain.