Understanding the Role of ECC608 TrustMANAGER and Kudelski IoT SaaS
In this blog post, we will explore the significance of the ECC608 TrustMANAGER combined with the keySTREAM™ Software as a Service (SaaS) from Kudelski IoT, its functions and its role in establishing security and reliability in an Internet of Things environment.

Dynamic Trust Management in the IoT Era
In an era dominated by technology and interconnected Internet of Things (IoT) systems, the concept of trust has taken on new dimensions. Whether IoT devices are conducting online transactions (Alexa ordering your next product, for example), sharing sensitive information (your order via Alexa was charged to your credit card) or collaborating in virtual spaces (your order triggered your garage to open for the package delivery), trust plays a pivotal role in shaping our digital experiences. So far IoT devices have been relying on static trust. But what happens if a system needs to be remotely updated, its ownership is compromised or the ownership changes very often? For example, imagine a connected/smart door lock on a short-term rental house and calculate the amount of renters this door lock will have to authorize and trust. The chain of trust needs to be dynamic and managed throughout the life of the lock. Enter the unsung hero of this digital trust ecosystem—the ECC608 TrustMANAGER combined with the keySTREAM™ Software as a Service (SaaS) from Kudelski IoT. In this blog post, we will explore the significance of this combined product, its functions and its crucial role in ensuring a secure and reliable IoT environment.
The IoT Trust Challenge
As we increasingly rely on digital platforms for various aspects of our lives, the need for trust becomes more apparent. From the consumer market to industrial, automotive and medical markets, IoT devices are constantly navigating a complex web of potential threats. Cybersecurity breaches, identity theft and data leaks are just a few of the challenges that underscore the importance of establishing, maintaining and managing trust in the IoT realm. All too often, IoT products are architected with a static chain of certificates without any protection of the private keys associated to the certificates in the IoT product (device certificate) nor on the production side (issuing certificate), nor at the product company level where root certificate authority (should) exists. Now that IoT devices have invaded the world, security experts start to question what happens to the IoT security model once devices are in the field. How is the security being both maintained but also kept up to date? And now comes more and more standards and regulations eyeing to mandate security updatability. What is to be done then? The answer—a cloud-managed TrustMANAGER secure authentication IC.
What Is the keySTREAM SaaS?
The keySTREAM SaaS is a product from Kudelksi IoT which serves as the cloud guardian of digital trust, overseeing the cryptographic authentication operations with the ECC608 TrustMANAGER secure authentication IC sitting in the IoT device. The keySTREAM role is especially crucial in environments where:
- Setting up a custom root CA and associated PKI is complex and/or costly and there is little to no time nor security expertise in the company. Yet, having a root CA is a very basic security foundation that must be architected in the product. In addition, standards, legislations or even your company IT policy will mandate one.
- Security credentials inside the IoT device need to be securely updated and managed when the IoT device is in the field.
- The custom PKI needs to be dynamically managed throughout the lifecycle of the IoT device.
- Product ownership needs to be transferred across multiple owners through its lifecycle.
- Supply chain logistics in handling custom security ICs due to the uniqueness of keys is an inventory management challenge.
- Maintaining good PKI and cryptographic hygiene is recognized as a foundational practice to remain in line with standard or even upcoming legislations.
What Is the ECC608 TrustMANAGER?
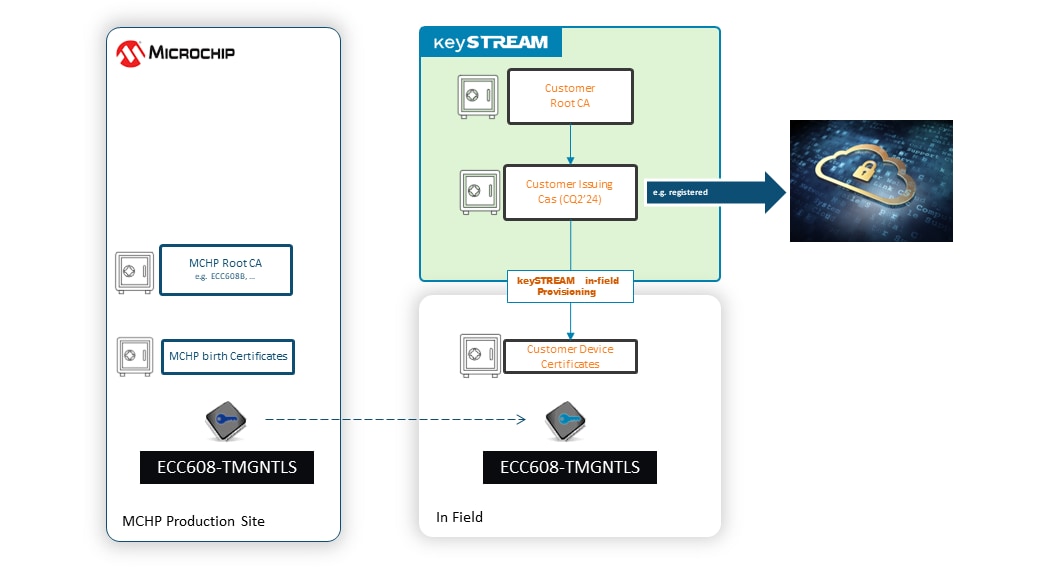
Microchip’s ECC608 TrustMANAGER is the secure authentication IC part of the CryptoAuthentication™ family which will securely store the cryptographic keys managed by the keySTREAM SaaS.
Out of the box, the device comes with a pre-provisioned set of keys that will be controlled by keySTREAM at the time the IoT device connects for the first time. This operation happens in-field and will be referred to as in-field provisioning of the PKI. Once the in-field provisioning has taken place, the fleet of devices containing the ECC608 TrustMANAGER has been “claimed” then “activated” in the keySTREAM account of the user:
- “Claimed” device: the purchased batch of ECC608 shows up in the keySTREAM account but not connected yet
- “Activated” device: the purchased batch of ECC608 has connected to keySTREAM and the in-field provisioning has taken place
The provisioning operation alone for a CM is a serial operation consuming programing time and adding manufacturing cost, plus it exposes security vulnerabilities in manufacturing when not using the Trust Platform solutions. For example, a key can leak out of your factory and copycats are now possible.
Behind the Scenes, What Has Taken Place?
To develop, maintain and support both a scalable authentication SaaS combined with an adequate dynamic secure key provisioning service for a given secure authentication IC would take years to implement. When you consider a classic IoT deployment runs between a few thousand to few million units for the most successful products, the economy of scale doesn’t make sense for a single company to invest in such development. Yet the need is clear. With the various security standards, regulations and even foundational recommended security practices, managed authentication becomes key.
With the keySTREAM SaaS and the ECC608 TrustMANAGER, this is what has happened in mere minutes:
- An HSM space is created in the keySTREAM account with multi-tenant capability.
- In that HSM space, a custom rootCA certificate and its associated private key are created in the protected environment of the HSM.
- During the creation of the root CA certificate, specific company information has been captured within the root CA, making it a custom root CA for your company and fleet of devices.
- During the PKI customization process, there has been no human interaction besides the user entries into keySTREAM.
- The amount of purchased “off the shelf” secure authentication ICs is claimed in seconds.
The contract manufacturer had no test time incurred nor interaction with the product company related to claiming the device. When the IoT device is in the field, the product company will be able to offer its end users a better management and PKI maintenance experience:
- When the device certificate date expires, the keySTREAM platform re-initiates a new certificate chain and binds it automatically to the ECC608 TrustMANAGER.
- If any trust in the device is broken, it can be remotely revoked and eventually refurbished entirely. Refurbishment helps companies to get devices back into their customer’s hands at lower cost.
Key Functions of TrustMANAGER and keySTREAM
- Set up a self-service custom PKI including the root CA with no interaction with Microchip nor any third party.
- Maintain the protection and availability of the certificate chain and its private key in HSM through time at all certificate levels including the root CA.
- Onboard IoT devices in any cloud platform your company uses without worrying about the scale of your fleet and the time it will take to upload large amounts of certificates and other cryptographic credentials in your cloud platform.
- Pay as you use for the IoT devices that will actually connect to your cloud platform. Think about the end customer that will never connect their IoT product to the internet. Don’t pay to activate devices in your cloud platform if the IoT device is not connected.
- Manage the health of the certificate chain: what’s your plan when certificate expiration dates expire or if you need to change the certificate chain? keySTREAM will manage each certificate level in your chain, revoke and refurbish a corrupted chain and schedule expiration date renewal.
To Get Started
Download the Trust Platform Design Suite and test the keySTREAM use case under the ECCC608 TrustMANAGER.
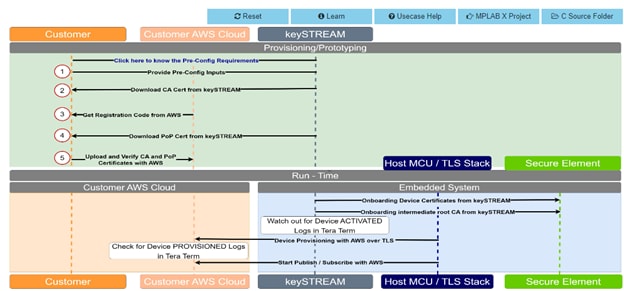
A complete getting started Chiptorial YouTube video is available to guide your first steps.
Read our case study on how keySTREAM and the ECC608 TrustMANAGER can help scale consumer applications in the building access management market.
The Future of Trust Management
As technology evolves, so too will the role of keySTREAM and the ECC608 TrustMANAGER. With the increasing importance of data privacy and regulatory compliance, TrustMANAGER will play a pivotal role in ensuring that organizations adhere to the necessary security practices.
Conclusion
In a digital landscape fraught with challenges, TrustMANAGER and keySTREAM serve as the unsung guardians of IoT device security. Their multifaceted role involves implementing robust security measures, staying ahead of potential threats and responding swiftly to incidents. As individuals and organizations continue to embrace the IoT era, understanding and appreciating the role of the TrustMANAGER becomes paramount in fostering a secure and trustworthy IoT ecosystem.