Design Imperative for the Internet of Things Era
Many large enterprises are focusing their IT investments on developing, deploying and maintaining cloud services. Now, developers are learning the latest cloud-related technologies and services.

In recent years, new ways of writing applications to make use of the cloud have been developed. Microservices—functions that operate independently to complete a single task—have become popular among cloud developers. One of their key benefits is their ability to be changed and updated independently from other services that are running concurrently on the platform. This model fits well with the continuous delivery practices adopted by many cloud developers.
Another growing trend is the use of containers, which enable the delivery of services along with the exact environment they require for deployment on servers or in Virtual Machines (VMs). Docker pioneered the use of containers and continues to set standards and lead the market in practices related to their use.
IoT Challenges for Cloud Developers
The Internet of Things (IoT) comprises a network of connected devices that includes sensors and intermediate devices known as edge gateways (or simply gateways) and makes use of these new cloud services. It has become notable for both the dramatic transformation it promises and for the perils and implementation challenges associated with it. The cloud ingests and analyzes data generated by IoT devices, allowing new insights from, as well as control of, remotely deployed assets. However, cloud-connected devices present a very different challenge compared to that associated with traditional PC platforms. Developing code to run on embedded devices requires knowledge of both hardware and software. The resource limitations of many of these devices further compounds the difficulties. Embedded devices are often required to run with very limited power budgets, have CPU cores with limited compute capability and are typically optimized for specific workloads. This means that developers must develop and maintain separate code for resource-limited devices and for the cloud.
Given the vast investment companies are making in cloud technologies, the ability to deploy containers and microservices to these edge devices holds tremendous appeal and value. Addressing the need to bring the power of cloud intelligence to mobile and IoT devices, Microsoft® has implemented an intelligent edge initiative called Azure IoT Edge. It enables Docker containers and microservices to be deployed on IoT edge gateways and other devices. This greatly simplifies the developer’s task, as code can be created once for the cloud and then be easily pushed to remote edge gateways. It increases design agility while reducing the time to market and the costs associated with maintaining two different code bases. However, this capability also introduces the essential need for security at the edge.
Securing the Edge
How should a device maker go about securing edge devices such as gateways? Gateways function as access points between sensors and cloud services. As such, they perform the vital function of connecting to and aggregating data from sensors and transmitting that data to cloud services for analysis and further operations. Gateways may also act as device management nodes performing a variety of command-and-control functions over associated sensors. For example, it is important for sensors to operate securely. Developers can ensure this by using a combination of authentication (sensor-to-gateway and gateway-to-cloud), encryption of transmitted data and regular updates of both sensor firmware and gateway software. These functions, if not properly secured, are vulnerable to malware or denial of service and man-in-the-middle attacks.
The standard requirements for securing these devices are:
- Secure boot: the device must implement a secure boot process all the way up from the hardware to the OS.
- Isolation of critical processes: security-critical processes, data and functions should be isolated and unreachable without proper credentials.
- Immutable ID: A unique device ID that cannot be corrupted is essential in many operations that take place during a device’s lifecycle.
- Secure storage: This is not limited to data coming out of sensors. It also includes sensitive material such as keys and certificates, which should be isolated and stored separately. Encrypting data is not just good practice—it is essential.
- Secure peripherals: sometimes peripherals perform security critical functions (e.g., biometric readers). These peripherals should only be configured to run, or be accessible to an application, in a secure state.
- Secure update: certificates and keys should be used to execute firmware and application updates to assure trustworthiness throughout the device’s lifecycle.
Solution Requires Software and Hardware
The right combination of hardware and software is required to implement these security measures. First, it is critical to choose the appropriate hardware platform. Device makers typically select a hardware platform that meets their design’s functional and power consumption requirements. However, security should be a primary criterion as well. The SAMA5D2 Arm® Cortex®-A5-based microprocessor (MPU) from Microchip provides several innovative security features including tamper resistance, secure RAM, secure fuses, True Random Number Generator (TRNG) and support for a variety of cryptographic algorithms.
To ensure that implementing security is as seamless as possible, it is important to make these features easy to use. This can be achieved with a system that combines Azure IoT Edge, the IoT Security Suite by Sequitur Labs and the SAMA5D2 MPU. See a video demonstration of Docker containers and microservices running on a SAMA5D2 MPU-based gateway that is connected to a SAM E54 microcontroller-based leaf node. The system controls a simple door lock that opens and shuts upon receiving a command from the gateway. This demonstration illustrates:
- Secure container provisioning to a SAMA5D2 MPU-based gateway
- Edge node attestation
- Container integrity checking and remediation
- Hardware crypto operations
- Certificate and key management in secured key store
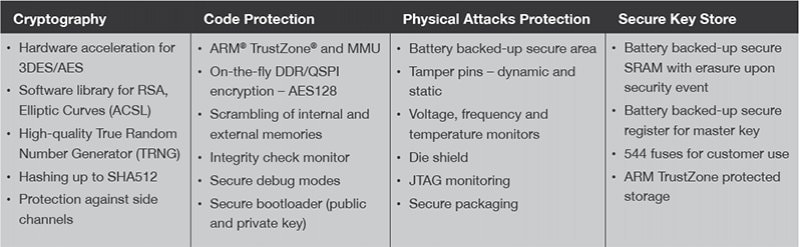
The IoT Security Suite is preconfigured to establish the secure enclave and make use of the SAMA5D2 MPU’s hardware based security components. The secure domain implements Sequitur’s trusted execution environment, CoreTEE™, on the gateway. CoreTEE provides a programmable, isolated environment for executing security-critical functions and storing sensitive data such as keys and certificates. The solution also includes Sequitur’s CoreLockr™, a software middleware layer comprising easy-to-use APIs for developers to access services and peripherals isolated by CoreTEE. The demonstration uses the SAMA5D2 MPU’s Integrity Check Monitor (ICM) to monitor the integrity of the OS hosting the Docker container by responding to and remediating a malicious code injection into the kernel. In this scenario, the malicious code injection invokes the ICM, causing an interrupt in the secure enclave that is detected by CoreTEE. CoreTEE solves the security breach by rolling the kernel back to a known and trusted image. A second scenario demonstrates how to use hardware security to authenticate the leaf node using an Arm TrustZone® technology-based secure enclave on the SAMA5D2 MPU and the hardware crypto engine on the SAM E54 microcontroller.
Conclusion
Given the magnitude of the risks and challenges, it is clear that the practice of layering on security used during the PC era will not be adequate to address the security requirements of the IoT era. The key to securing the IoT is a combination of a hardware device with advanced security technologies and trusted software that is designed make it easy for developers to implement these technologies in their new designs. Microchip and Sequitur Labs are committed to advancing new security solutions for use in IoT and other embedded devices.
For more information, visit our SAMA5D2 page.