TrustFLEX ATECC608 Secure Element for TLS-Based Networks
Leverage the Simplicity of Thumbprint Certificate Authentication

Benefits of Using the TrustFLEX ATECC608 With TLS
- Leverage multiple use cases with our pre-configured devices
- Use your own certificate authority
- Leverage the simplicity of thumbprint certificate authentication
- Implement a unique, trusted, protected and managed device identity
- Turn-key code examples
- Leverage Microchip’s secure provisioning service
- Simplify logistics of shipping private keys and reduce manufacturing costs
- Microcontroller-agnostic implementation
- JIL rated “high” secure key storage
- Protection against known tamper, side-channel attacks

TrustFLEX ATECC608C-TFLXTLS Use Cases
Each of the device slots is preconfigured to offer the following use cases:
- Custom certificate authentication
- Token authentication
- Secure boot (with key attestation)
- Over-the-Air (OTA) verification
- Firmware Intellectual Property (IP) protection
- Message encryption
- Key rotation
- I/O protection key
- Host accessory authentication
Ready to Get Started with Trust&GO and a TLS Stack Provider?
mBedTLS
- Buy the CryptoAuthentication™ SOIC Starter Kit (DM320109)
- Download the code example on GitHub
- Buy the ATECC608C-TNGTLS
WolfSSL
- Buy the CryptoAuthentication SOIC Starter Kit (DM320109)
- Request code example from WolfSSL
- Buy the ATECC608C-TNGTLS
Linux® OS
- Buy the SAMA5D27 SOM1 Kit1 (ATSAMA5D27-SOM1-EK1)
- Download the code example on GitHub
- Buy the ATECC608C-TNGTLS with the CryptoAuthentication UDFN Socket Board (AT88CKSCKTUDFN-XPRO)
Tools and Software
- Demo & Evaluation Boards
- Development Environment

An SOIC Crypto Authentication Xplained Pro starter kit for easily evaluating and developing with Crypto Authentication Security devices.

The SAMA5D27-SOM1-EK1 is a fast prototyping and evaluation platform for the SAMA5D2 based System in Packages (SiPs) and the SAMA5D27-SOM1 (SAMA5D27 System On Module).

The AT88CKSCKTUDFN-XPRO is an XPRO extension board that attaches 8-pin UDFN CryptoAuthentication™ devices to Microchip MCU's that support an XPRO interface. All Microchip CryptoAuthentication™ devices regardless of interface can be used with this board.

The CryptoAuth Trust Platform provides a compact development solution for developing IoT solutions with the ATECC608B-TNGTLS and ATECC608B-TFLXTLS and ATECC608B-MAHDA devices or the ATECC608C equivalents.
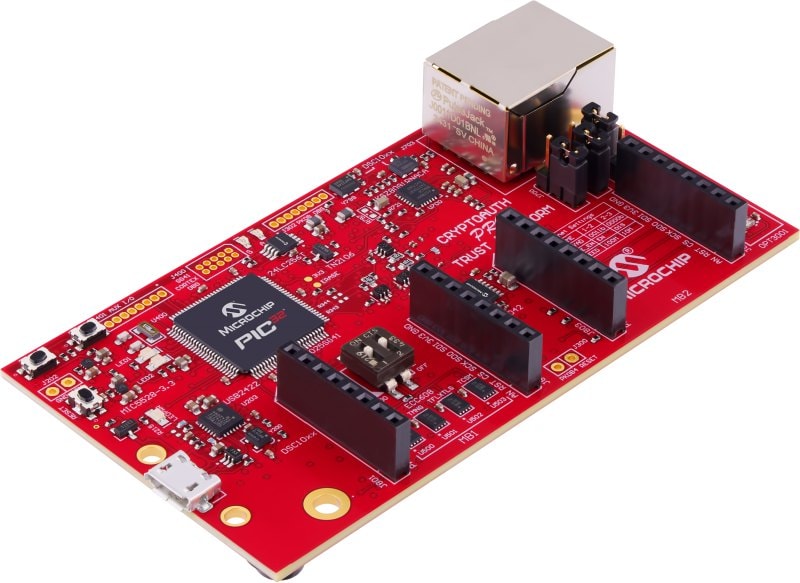
The Microchip CryptoAuth Pro Trust Platform is an enhanced version of the CryptoAuth Trust Platform Board containing and has a Arm® Cortex®-M4F Microcontroller, four on-board CryptoAuthentication devices, two mikroBUS™ sockets, and an on-board 10/100 Mbit Ethernet phy. Programming can be done via the on-board PKoB4 debugger which is compatible with MPLAB®X IDE. The board has been developed to work with Microchip's Trust Platform Development Suite of tools.

The Trust Platform Design Suite (TPDS) is our onboarding tool for our security-related solutions. The full onboarding experience includes, but is not limited to:
- Training and education about security concepts
- Prototyping, including dummy key generation and code examples, available via our interactive application notes
- Access to our provisioning system through a secure sub-system configurator and secure exchange process

MPLAB X IDE is a highly configurable software platform that provides powerful, free tools for developing, debugging and qualifying embedded designs that use microcontrollers and digital signal controllers.